We had previously discussed real-world for-profit SS7 attacks that successfully helped deplete consumer bank accounts in Germany in an article in early 2017.
The SS7 part of the attack consists in intercepting 2FA tokens that are being sent by the bank to the customer’s phone via SMS, so that these tokens can be used by the attacker to validate outgoing online wire transfers initiated via online banking (a function commonly available in online banking interfaces outside the United States).
Now, two years later, one would expect that with wide ranging deployments of SS7 firewalls, such attacks would no longer be possible, at least not in developped countries which were among the first to implement countermeasures (the European Union mandated that operators protect their SS7 interconnects as far back as 2015).
Unfortunately, the reality is different, as reported recently by an article in Motherboard: Motherboard reports that bank accounts at the UK’s Metro Bank were recently depleted by attackers using SS7-based attacks against one or several UK mobile operators. This is particularly suprising consider that all mobile networks in the UK have already deployed on-premises SS7 firewalls, but consistent with reports from leading firewall vendors that fraudulent SS7 traffic is on the rise year over year.
This incident reminds us of two things:
– not all SS7 firewalls are created equal, and mobile operators ought to test that their firewalls are protecting them even against more elaborate Category 3 attacks, which this one falls under.
– mobile networks need to be tested on a regular and continuous basis, to ensure that protection remains in place over time. All too often, we see firewall rules being altered or dropped inadvertently several months after a firewall is deployed into a mobile network, and without regular external testing, it is nearly impossible to catch such an error until it is exploited.
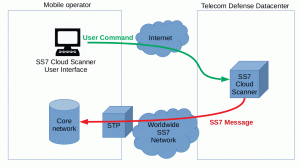
The Telecom Defense Limited Company’s remote SS7 penetration test is able to test a mobile operator’s network quickly and inexpensively against all SS7 attack scenarios, including Category 3 attacks such as this one.